Overview
Directories
With Mamori you can access resources using identities defined in
- Mamori's built-in directory
- one or more integrated AD/LDAP directories
- one or more integrated cloud directories (Azure, Okta or Duo)
Any identity from any directory can be multifactored with
- Mamori's built-in multifactor
- integrated 3rd-party multifactor
When Mamori receives a connection, it first validates the connection with the directory. If the connection is valid, then Mamori sends the configured multifactor request for the user.
Multifactor Support
Mamori built-in multifactor includes
- mobile push notifications via the Mamori.io mobile application
- push totp via a web browser
- YubiKey
All of these methods work from standard tools accessing all resources types (web, ssh, db and ip resources).
User Multifactor Configuration
When a user logs into the Mamori portal if their multifactor is not configured, then a QRCode will be displayed. To complete the registration process the user needs to scan the QRCode with the appropriate mobile application.
logins from standard tools will fail if a user has not configured their multifactor. They must login to the Mamori portal at least once to configure it.
Mobile Push
With Mobile push multifactor the user accepts or denies the access request on their Mamori mobile application. This is the recommended form of multifactor as it is easy for users to work with.
Requirements
Mamori mobile application installed on user's device
IOS : search for Mamori 2FA
Android : search for Mamori
Mamori server requires HTTPS (port 443) send and receive from:
fcm.googleapis.com/*
oauth2.googleapis.com/*
accounts.google.com/*
Push Timed One-Time Passwords (TOTP)
Mamori supports TOTP multi-factor authentication (MFA). Users can access resources and enter the TOTP token when requested via a MFA notification. The rotating token can be generated by Authy application like Google Authenticattor, Microsoft Authenticator and the Mamori Mobile App.
Requirements
Any Authorization App installed on a user's device that scans one-time password QR codes.
No internet access required
YubiKey
Mamori supports both online and offline YubiKey. The online method requires that the mamori server have internet connection and the offline method requires changes to the YubiKey config.
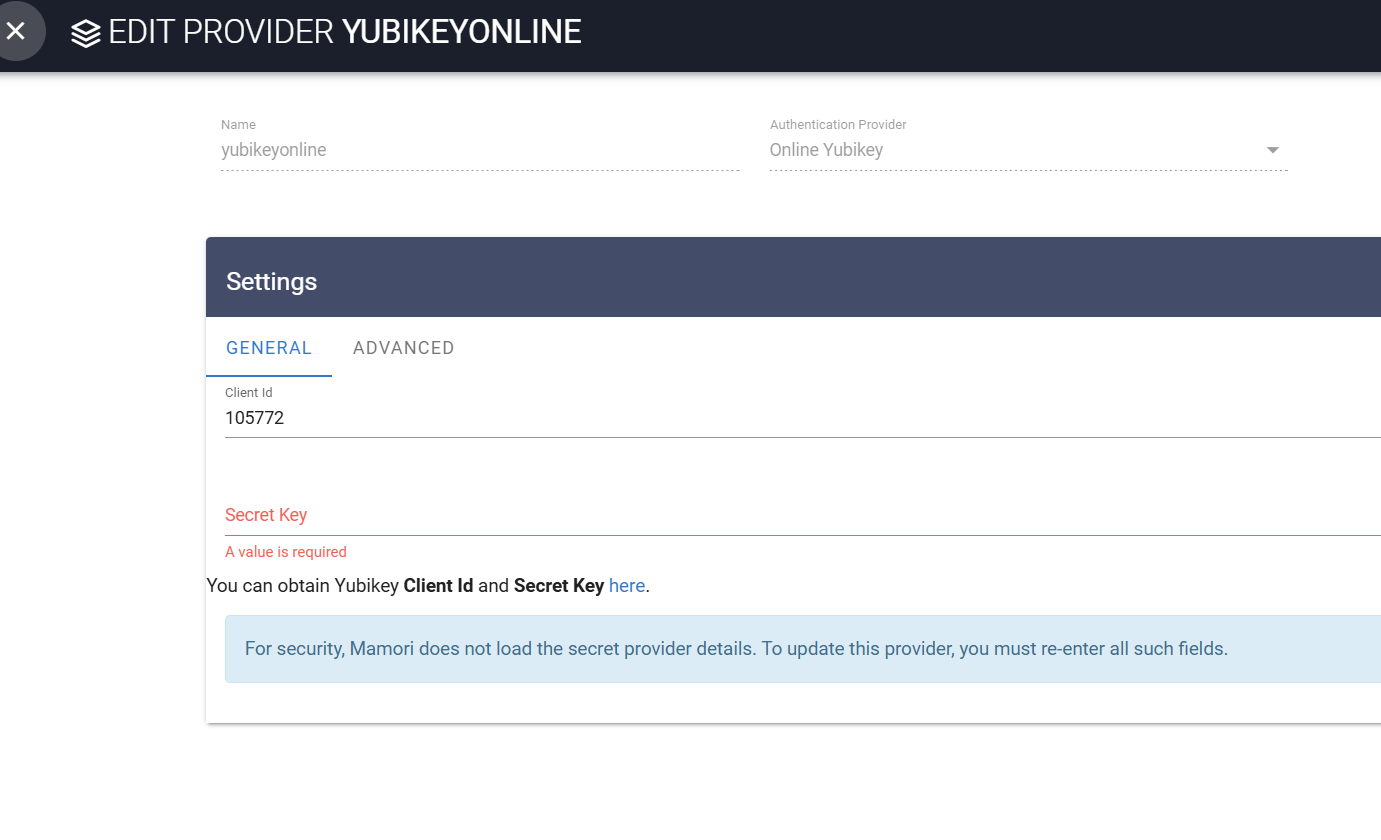
To configuring online YubiKey
>Click Server Settings > Authentication ProvidersClick
Name the provider
Choose Online YubiKey from the Authentication Provider list.
Fill in these fields on the Settings tab:
Field Description Client ID Your YubiKey client id Secret Key Your YubiKey Secret Click Save
Click Validate Provider to test
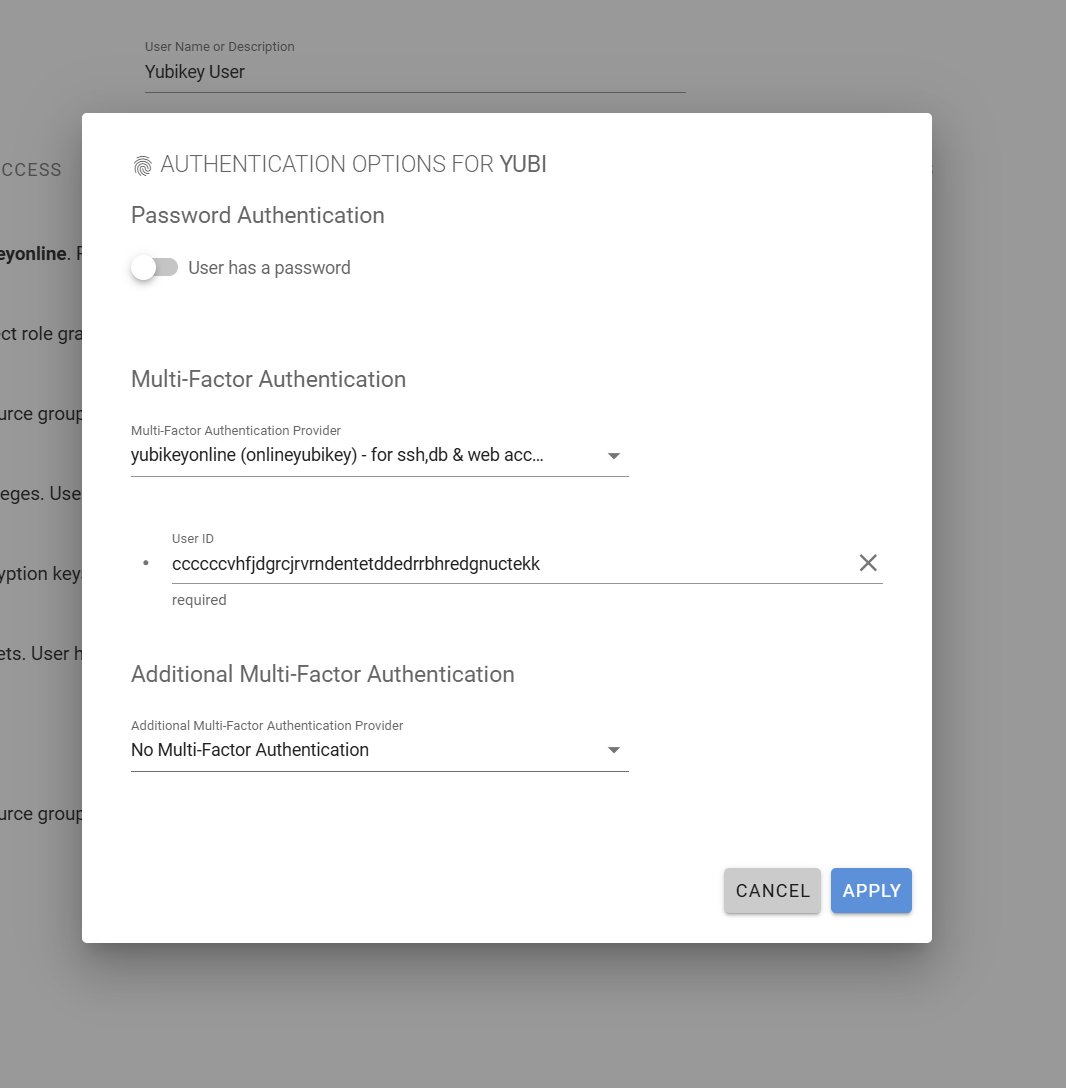
Edit a user on role and set the Authorization MFA to the YubiKey Provider