Access Policies
Access policies provide users with either permanent permissions on resources or the ability to request permissions on a resource. Administrators manage both who is able to request and endorse which policies and resources.
- Grants - permanent or time based permissions granted to a user or Mamori role.
- On-demand policies - Request and endorse a policy that grants permissions on a custom set of resources.
- On-demand resource policies - Request and endorse access to a particular resource.
Additionally databases have data access and data privacy policies
Grants
Click on the desired resource type main menu item
- SSH Logins
- Remote Desktops
- HTTP Resources
- Roles
- Secrets
- WireGuard > IP Resources
Find the resource and click on Manage User Grants or Manage Role Grants row menu item
Click on advanced options to set time based grants
Click on the grantee to toggle the grant
On-demand policies
Create
To create an Access On-Demand policy follow the steps below
Prerequisites
Required Permissions
To make or approve requests a user must have the REQUEST privilege, either directly or via a role. Additionally, To request a particular policy a user must have the request role specified in the policy.Click Policies
Click Access On Demand
Click Add
Next, enter the details
Section Field Description Policy Name name user will request Description Description of grant policy will provide Type Policy - For custom set of resources
Resource - Invoked by requestable resource grantsRequest Role Role required to request the policy Alert (optional) Alert channel for new quests Endorsement Role(s) Roles required to endorse the policy Level Count Number of endorsements required per role Allow self endorsement Defaults to false
Allows endorser to endorse their own requestDefault Message Default approval message to provider user Approval Alert (optional) Alert channel for approved policies Deny Alert (optional) Alert channel for a denials Execute Alert (optional) Alert channel for executed policies Execute on approval defaults to false. When true the grant expiration starts on approval. When false it starts when the applicant executes the policy. Script Parameters (optional) Custom request parameters to collect from the applicant Statements Enter One or more Grant Statements. Script Statement Syntax Click Create
Request
Click Access Requests > Request a Policy
Find the policy and click Request
Enter the policy paramters and click Request
Endorse
Click Access Requests > Endorse Request
Find the policy request and click Endorse
Enter a comment and confirm
Script Syntax
Mamori On Demand policy script syntax is an easy to use SQL-like syntax. Statements can have parameters and clauses that specify when the grant is valid.
A policy script can have many statements and one statement can :
- Grant a role, privilege, or object permission
- Grant access to an ssh login
- Grant access to use an encryption key
- Grant reveal masked data for specified database objects
- Grant access to an IP resource
- Insert, Update and delete table data
- Run Insert as Select across databases
Parameters
The syntax uses :customvalue for statement parameters.
Validity
GRANT and GRANT REVEAL statements can include VALID date and time.
| Clause | Description |
|---|---|
| VALID BETWEEN :date1 AND :date2 | valid between two dates |
| VALID FROM :date1 | valid from a date |
| VALID UNTIL :date1 | valid from a date |
| VALID FOR :amount [seconds, minutes, or hours] | valid from a specified unit of time |
Enter dates in format YYYY-MM-DD
A permanent grant is one without a VALID clause.
Grant a privilege
GRANT REQUEST TO :applicant VALID FOR :time minutes;
Grant a Role, Policy, IP resource
GRANT myrole TO :applicant VALID BETWEEN :date1 AND :date2;
GRANT mypolicy TO :applicant VALID BETWEEN :date1 AND :date2;
GRANT myipresource TO :applicant VALID BETWEEN :date1 AND :date2;
Grant Encryption Key Usage
GRANT KEY USAGE on :encryptionkey TO :applicant VALID FROM :date1;
Grant Data Reveal
GRANT REVEAL * ON "datasource"."database"."schema"."table" TO :applicant valid for :time minutes;
Grant SSH Login
GRANT SSH mysshlogin TO :applicant VALID FOR :time hours;
Grant on DB Object
GRANT SELECT on "datasource"."database"."schema"."table" TO :applicant;
GRANT UPDATE on "datasource"."database"."schema"."table" TO :applicant;
GRANT INSERT on "datasource"."database"."schema"."table" TO :applicant;
GRANT DELETE on "datasource"."database"."schema"."table" TO :applicant;
GRANT CREATE TABLE on "datasource"."database"."schema" TO :applicant;
GRANT DROP TABLE on "datasource"."database"."schema" TO :applicant;
GRANT is overruled if there is a DENY already on the object.
On-demand resource policies
Manage
Click on the desired resource type main menu item
- Datasources
- SSH Logins
- Remote Desktops
- HTTP Resources
- Roles
- Secrets
- WireGuard > IP Resources
Find the resource and click on the Manage Request Grants row menu item
Request
Click Access Requests > Request a Resource
Click on the resource type
Find the resource and click on Request Access row menu item
Enter the policy fields and confirm
Endorse
Click Access Requests > Endorse Request
Find the policy request and click Endorse
Enter a comment and confirm
Data Permission Policies
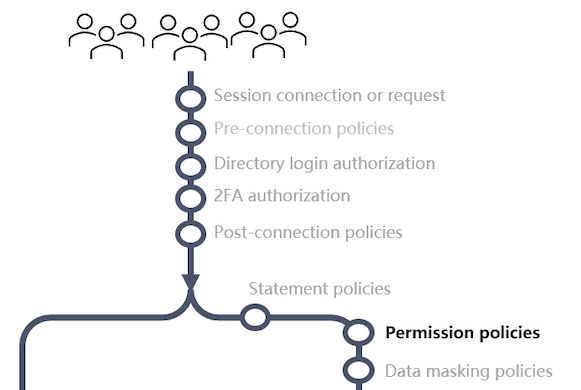
Database permission policies allow granular segmentation of the permissions that an existing database credential has. You can craft policies that restrict SQL operations and access without needing to create additional database credentials in the database.
For example, a user can be assigned access via a DBA credential with a permission policy that only allows select. When the user access the database from any tool only select statements will be allowed. All other statements will be blocked.
Details
Triggered : Right before a database command is sent for execution
Best for : Blocking unauthorized database commands, object access or limit rows returned.
Data access permission policies allow control over what statements will be sent for execution in the database. Additionally incoming SQL is potentially re-written based on the configured row and column security.
Common Configuration
Data Permission Policy configuration
Managing
To manage data access policies
- Edit a user or role
- Click on Database & Data Access > Object Privileges
This displays the current permissions for the grantee
To remove a permission
Find the permission and click on the Revoke row menu item
To add a permission
- Expand the Add new grant panel
- Fill in the grant details
Section Field Description Permission Type Grant or deny Permission Scope The level the permission applies to
Datasource, Database, Schema, ObjectPermission The permision list for the selected level Permission Type Grant or deny Permission Type Grant or deny Set Database Object This section allows you to specify the specific database objects. Leaving it all blank means all datasources, all databases, all schemas and all objects.
The appropriate fields will display based on the permission scopeDatasource Enter blank, * or a specific item Database Enter blank, * or a specific item Schema Enter blank, * or a specific item Object Enter blank, * or a specific item Set Grant Expiry This section allows you to specify the validity clause
Always Valid
Valid From
Valid Between
Time LimitedValid From & Between Ented date in the format YYYY-MM-DD HH:MM Time limited Enter amount and select unit Set Row Restriction Applies a limit or where condition
Only displays if SELECT, DELETE, UPDATE permissions are selectedApply or override a limit on rows Toggle true/false
if true enter a limit amount
If false check overrideRestrict Rows with a where clause Toggle true false
enter a valid SQL where condition pre-fixing column names with $.NOT (($.OWNER like 'SYS%'))Click Add
Data Privacy Policies
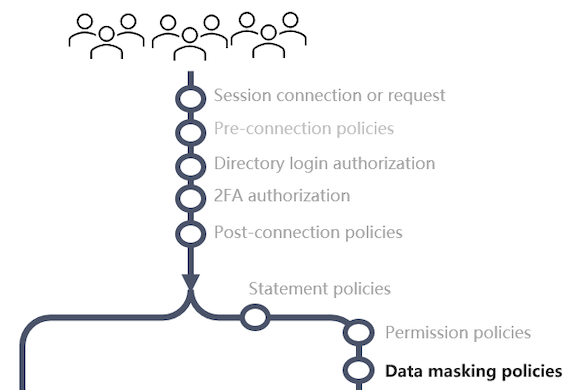
Details
Triggered : Right before a database command is sent for execution
Best for : Column security and data masking.
Data privacy policies allow you to hide or mask column based on a users permission.
Managing Available functions
The mamori server contains a default set of masking functions that can be used for javascript and the main RDBMS SQL types.
Click Policies > Masking Functions
Edit, Add or delete functions in the grid.
Managing Privacy Policies
For SQL
Click Policies > SQL Data Policies
Click
Enter the fields
Field Description Name Reference for the policy Description Policy Description Priority In the event a user has conflicting rules for the same column, then the lower numbered policy will apply Click Create
Click Masking Rule
- Select the columns
- Select the masking rule to apply
- Click OK
For NoSQL
Click Policies > NoSQL Data Policies
Click Mongo DB Filter
Enter the fields
Field Description Filter Name Reference for the policy Datasource/Collection Collection this applies to Click Create
Click Transformations
Enter the fields
Field Description Role Role this will applied to Field/Attributes json path selector JS function Select the function to apply Arguments Addition parameters passed into the function Click OK