For Administrators
Mamori Version & License
To view the server version and manage the Mamori license
Click > Help
Click > Mamori License
Managing Proxy Listeners
To view and manage the database and SSH proxy ports
Click Server Settings
Click Proxies
| Proxy | Default Listener Port |
|---|---|
| SSH | 1122 |
| Postgres | 5432 |
| Oracle | 1521 |
| MySQL | 3306 |
| Microsoft SQL Server | 1433 |
| mongoDB | 28017 |
| Other JDBC | 1527 |
Datasource Drivers
To view and manage the datasource drivers
Click Server Settings
Click Drivers
Click
Set the name, type
Select the upload the driver resource file
Click Ok
Database Drivers
Common database driver links
| Database | Download | Notes |
|---|---|---|
| Amazon Redshift | Download redshift JDBC driver | Can use native postgres proxy |
| Aurora MySQL | See MySQL | |
| Aurora Postgres | Postgres is preinstalled with Mamori server | |
| BigSQL | Download BigSQL/DB2 drivers | 50000 |
| Cassandra | Download Apache Cassandra driver | |
| Derby | Download Derby drivers | |
| EDB Postgres | Download EDB Postgres driver | Postgres is preinstalled with Mamori server |
| Gemfire (AKA Pivotal Gemfire) | Download Pivotal Gemfire driver | |
| Hadoop | [Contact Mamori for help with Enterprise Installations](mailto: support@mamori.com?subject=Hadoop%20enquiry) | |
| Hawq | Download Hawq driver | |
| Hive Cloudera | Download Hive Driver 2.5.19 from Cloudera | |
| Hive Hortonworks | Download Hortonworks Hive driver | |
| Greenplum ODBC | Download GreenPlum ODBC | Can use the native postgres proxy |
| IBM DB2 LUW | Download from DB2 Drivers | |
| Impala JDBC | Download Impala JDBC driver | |
| InfiniDB | See MySQL | |
| Mysql8 | Download MySQL driver | |
| Netezza | Netezza Software and Client Applications | AKA IBM PureData. You'll need an IBM login to access their downloads page |
| Oracle | Download Oracle JDBC driver | |
| Postgres | Download Postgres driver | Postgres preinstalled with Mamori server. |
| Redshift | See Amazon Redshift | Can use the native postgres proxy |
| SQL Server | Download sql server JDBC driver Download JTDS SQL Server JDBC driver | |
| Sybase ASE / SAP ASE | View SAP ASE drivers Older Sybase ASE drivers (v 0.1 to 1.3.1) | SAP requires authorization to download drivers. |
| Sybase IQ | Download sybase iq JDBC driver | |
| Teradata | Download Teradata JDBC driver | You'll need to a Teradata account to download drivers. |
| Vertica | Download vertica JDBC driver | You'll need a vertica account to download drivers. |
Please advise Mamori support if you find outdated drivers in this list.
Support
Raising a support issue
Freemium users can contact support by sending an email to support@mamori.io
Paying customers can click here to raise a ticket
In your email please included:
- Description of what were trying to achieve when you go the error.
- Screenshot of error
- Support bundle (If the file is over 10MB please provide a link to download the file. Do not attach it)
Creating a bundle
To generate a support bundle, follow the instructions below.
Click > Help
For all-in-one deployments
Click > Download Support Bundle
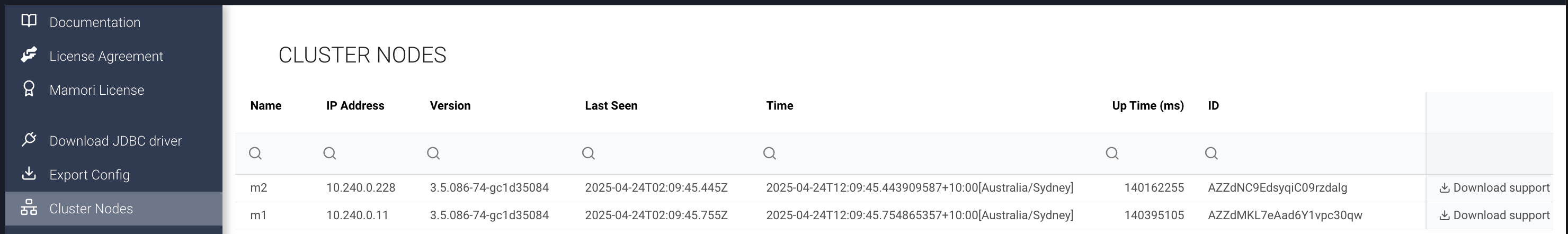
For HA deployments
Click Cluster Nodes and then download on the the node
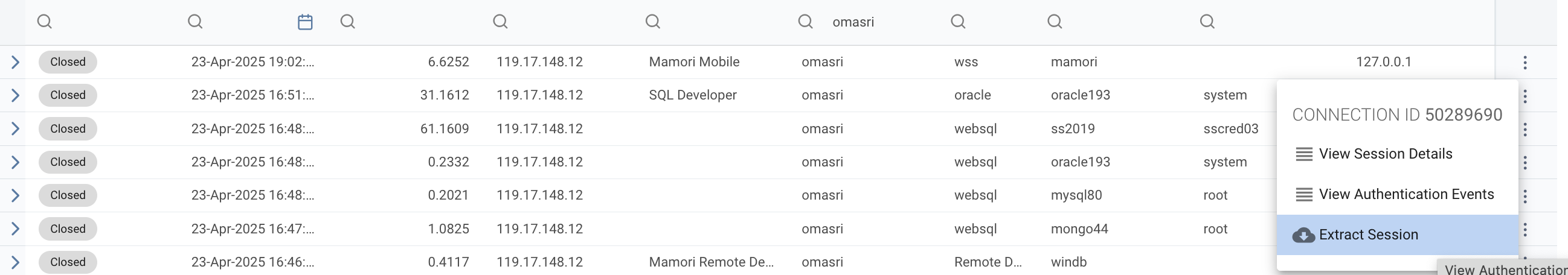
Extracting a session
Sometimes support will need you to extract the contents of a session to help resolve an issue. This can be done by:
Navigate to Logs > Connection Log
Find the session that has the issue and click on the row menu
Click Extract Session
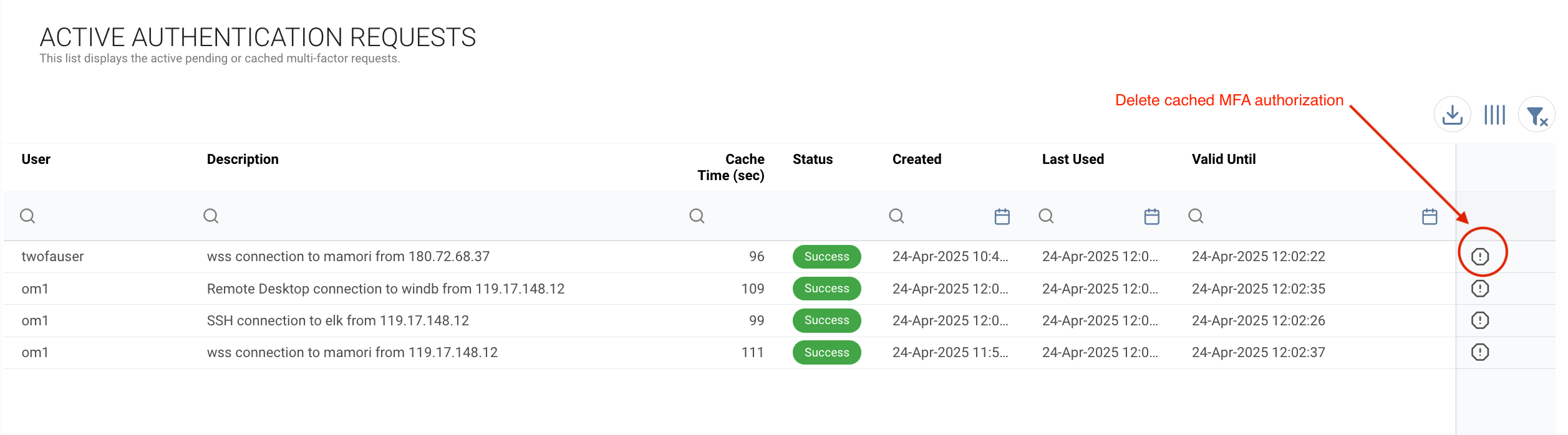
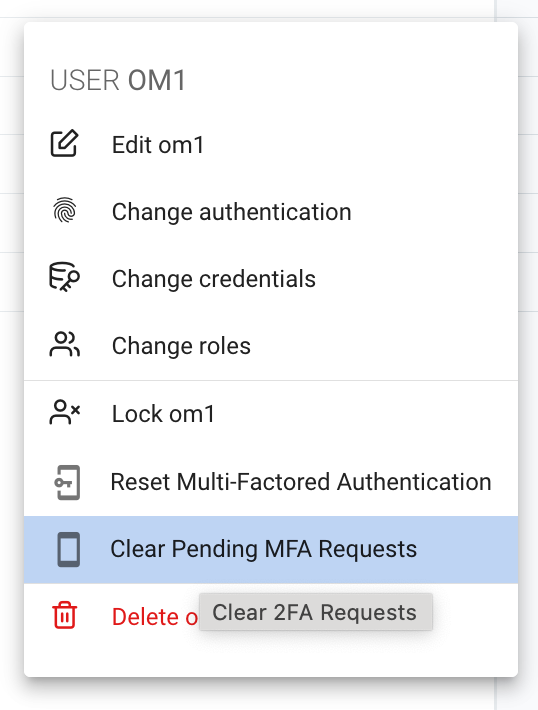
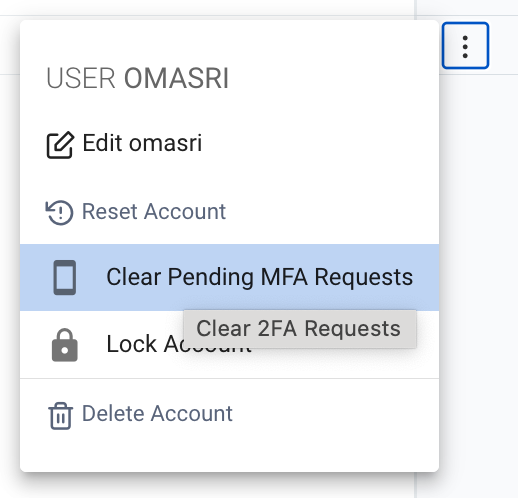
Reseting MFA requests
All cached MFA requests can be managed from the MFA request log grid
Navigate to Logs > MFA Requests
You can remove a particular cached MFA request by clicking delete on the request row.
You can remove all the cached MFA requests for a user from the user grid row menu.
Checking HA cluster status
Click > Help > Cluster Nodes
Sharing Grafana Dashboards
Grafana is a well documented open source application. Their documentation has instructions on how to share dashboards between grafana servers via the export/import functions. See their documentation to learn more. https://grafana.com/docs/grafana/latest/dashboards/share-dashboards-panels/
SQL-Based Integration
To interact and integrate with Mamori via SQL instead of API requests you need to
- download and install the Mamori ODBC (32-bit or 64-bit) or JDBC (64-bit) driver
- connect any database tool to the mamori database
Downloading the driver
Go to the Mamori server login page and do not login
Click on "download drivers"
Select your driver and download it
Unzip the media and install
Windows ODBC
Run the driver MSI installer
Launch windows ODBC Data Source Administrator
Add a DSN
Select the Mamori Driver (Mamori 64)
Enter the following in the DSN Dialog
Field Default Value Description Datasource Name Enter the DSN name Server Host Name or IP Enter the IP address of the Mamori server Server Port 1527 Remote System Mamori The datasource to connect to Datasource Name Enter the DSN name Credentials Enter a Mamori login username and password Click OK
JDBC
Open the driver manager of your SQL tool & Add a driver
Add the mamori jar file
Classpath is io.mamori.jdbc.security.Driver
Connection String
connection stringjdbc:mamori://YOURMAMORISERVER:1527/mamori;schemapattern=true
Manage Encryption & SSH Keys
With Mamori's built-in key management service you can define or store
- AES keys for symmetric data encryption
- RSA key pairs for asymmetric data encryption
- SSH private keys for SSH network tunnels and logins
Symmetric Encryption
To add an AES encryption key
Click Server Settings
Click Keys
Click
Set the key properties
Field Description Key Name Name passed into encryption function Key Type Select AES Key Enter key content Password (Optional) Require a password to encrypt/decrypt data Click OK
Asymmetric Encryption
To add a part or create an RSA encryption key pair.
Click Server Settings
Click Keys
Click
Set the key properties
Field Description Key Name Name passed into encryption function Key Type Select RSA Method Select Automatic to generate a pair or Manual to paste in an existing public or private key Size Defaults to 1024 Click OK
SSH
To add an SSH key
Click Server Settings
Click Keys
Click
Set the key properties
Field Description Key Name Your reference for the key Key Type Select SSH Key Paste in the private key that you generated with ssh-keygen -t rsa Do not add a keyphrase to your key
Password Leave Blank Click OK
Manual Grant
- Click Keys
- Find the resource in the grid and click
- Click Manager Assigned Users or Manager Assigned Roles
- For time grants toggled advanced options
- Click on the grantee to add or remove the grant
Remote Network Gateway
Open VPN
Click Server Settings
Click Networks
Click
Set the key properties
Field Description Name Your reference for the network Type Open VPN VPN Credentials Username and password Open VPN File The open vpn configuration file (*.opvn) Click Create Connection
SSH Tunnel
Prerequisites
Place the public key in the target machine's authorized keys
Click Server Settings
Click Networks
Click
Set the key properties
Field Description Type SSH Tunnel Name Your reference for the tunnel SSH User ssh target account name SSH Host ssh target host name SSH Post target ssh port Local Port the port that will be used locally Target Host default to localhost Port port being mapped to on the target Private Key Select the private key to use for the tunnel Click OK
Event Handlers
Event handlers allow you execute custom code in your security policies. The event handler types are :
- Triggered Event
- HTTP Request
- HTTP Response
- Websocket Text Frame
To create an event handler
Click Server Settings > Event HandlersClick Add
Next, enter the details
Field Description Name reference Type the type details enter the handler code Click Create to save the event handler
Examples
Row Limit Event Handler
var alert_name = mamori.getServerProperty("row_limit_alert", "default_row_limit_violation");
var rs = mamori.query("select username, system_name, database_name, schema_name, table_name, row_limit, row_count, limit_period, description from sys.row_access_limit_violations a join sys.row_access_limits b on a.row_limit_id=b.id");
try {
while(rs.next()) {
var facts = mamori.makeFacts(rs, ["username", "system_name", "database_name", "schema_name", "table_name"]);
LOGGER.info("Row limit violation found: " + facts.toJSON());
mamori.alert(alert_name, facts);
}
} finally {
rs.close();
}
Unmasked PII Columns
var rs = mamori.query("select t.systemname, t.schemaname, c.databasename as database_name, t.tablename as table_name, c.columnname as column_name, c.columndatatype as data_type from (select * from SYS.MAMORICOLUMNS a join mamori.mamorisys.rms.syssearchexpressions b on lower(a.columnname) like b.rule where SYSTEMID = 16 and columndatatype like '%char%' ) c join (select * from SYS.MAMORITABLES where SYSTEMID =16) t on c.referenceid=t.tableid and c.systemname = t.systemname where not exists (select 'x' from SYS.MASKING_EXCLUSIONS e where e.objectid = t.tablename) and not exists (select 'x' from SYS.COLUMN_MASKING_RULES m where m.systemid=c.systemid and m.databasename = c.databasename and t.schemaname = m.schemaid and m.tableid = t.tablename and m.columnname = c.columnname and m.operation in ('MASKED','TRANSFORMED'))");
try {
out.write("**** Unmasked PII Column check start.");
while(rs.next()) {
var facts = mamori.makeFacts(rs, ["systemname", "schemaname", "database_name", "table_name", "column_name","data_type"]);
LOGGER.info("Unmasked PII Column violation found: " + facts.toJSON());
out.write("Unmasked PII Column violation found: " + facts.toJSON());
mamori.alert('unmasked_pii_columns', facts);
}
} finally {
rs.close();
}
Alert Channels
You can define an alert channel with one or more alert action.
- Email Role (Emails all users with a Mamori role)
- HTTP operation (POST, GET, PUT)
- Mamori notification (Alert Mamori Mobile App)
- Event
Alert channels are used in connection policies, statement policies and access on-demand policies.
To create an alert channel
Click Server Settings > AlertsClick Add
Next, enter the details
Field Description Alert Name reference for alert channel Alert Type the type of alert Alert details enter details for alert type Click to add another alert in the channel
Click Create to save the channel
Parameters
To use parameters place the parameter inside brackets {{parameter}}.
Parameters for tcp events
- username
- source (client IP address)
- device (user's device name)
Parameters for connection and session events
- username
- source (client IP address)
- target (target datasource)
- context (client information)
parameters for on-demand events
- applicant
- applicant_message
- agent
- agent_message
- procedure (the policy name)
- request_key
- status
Email Alert
Next, enter the details
| Field | Description |
|---|---|
| Email Addresses | comma separated list of emails or parameter {{applicant_email}} |
| Subject | email subject |
| Body | email content |
Email Role
Next, enter the details
| Field | Description |
|---|---|
| Role | A role name or parameter {{endorsing_role}} |
| Subject | email subject |
| Body | email content |
Example Email Body
DB access alert
username: {{username}}
accessing datasource {{target}}
client ip: {{source}}
context: {{context}}
contextjson: {{contextjson}}
Mamori Notification Alert
Sends a notification to the Mamori mobile application.
Next, enter the details
| Field | Description |
|---|---|
| Recipient Name | Mamori user name or parameter for example, {{applicant}} |
| Notification Type | Message (Message Web Authenticator)PushMessage (Message Mamori Mobile App) |
| Body | content |
Messages content is a JSON object
title
message (HTML string content with parameters)
navigate-status (optional navigation)
"endorsed" "declined"navigate-to (optional navigation)
"0" Policies page "1" Requests page "2' Request history page "3" Pending Approvals "4" Approval History "5" Active Permissions "6" Active Session "7" Approved Requests
Example Endorsement Alert
{
"title":"Endorsed Notification",
"navigate-status":"endorsed",
"message":"<p style='text-align:left'>
<br>
<strong>policy: {{procedure}}</strong><br>
applicant: {{applicant}}<br>
message: {{applicant_message}}<br>
agent: {{agent}}<br>
reason: {{agent_message}}<br>
</p>"
}
HTTP Alert - Slack
Sends a notification to slack
Select HTTP as the alert type and enter the details
| Field | Description |
|---|---|
| HTTP Operation | POST |
| Header | |
| Url | your slack message hook |
| Body | content (JSON object) |
| Content Type | application/json |
Endorsement alert example
{"attachments": [
{ "color": "#2eb886",
"pretext": "A policy has been endorsed",
"author_name": "Mamori",
"title": "Policy Request for {{applicant}} endorsed by {{agent}}",
"text": "A policy request with the following parameters has been issued.",
"fallback": "Request Details",
"fields": {{contextjson}},
"footer": "This is a Mamori Policy Notification",
}
]
}
Intrusion alert example
{
"attachments": [
{ "color": "#f93836",
"pretext": "A wireguard peer has been blocked",
"author_name": "Mamori",
"title": "Wireguard peer blocked - {{device}}",
"text": "User: {{username}} - client ip: {{source}}",
"footer": "This is a Mamori Peer Notification",
}
]
}
HTTP Alert - Line
Sends a notification to Line
Select HTTP as the alert type and enter the details
| Field | Description |
|---|---|
| HTTP Operation | POST |
| Header | Authorization: Bearer YOURLINEGROUPKEY |
| Url | https://notify-api.line.me/api/notify |
| Content Type | application/x-www-form-urlencoded |
| Body | content |
Message content is a URL-encoded string
Example Endorsement Alert
message=A%20policy%20has%20been%20endorsed.%0D%0APolicy%20Request%20for%20{{applicant}}%20endorsed%20by%20{{agent}}%0D%0ARequest%20key:%20{{request_key}}%0APolicy%20name:%20{{procedure}}%0AApplicant%20message:%20{{applicant_message}}%0AReason:%20{{agent_message}}%0AStatus:%20{{status}}¬ificationDisabled=false
Event
| Field | Description |
|---|---|
| Event Handler | Select the event handler to invoke for this alert |
Application Proxies
Configuration file JSON format
JSON files can be used to configure an application proxy.
To use a JSON configuration file when running a proxy in standalone mode pass in the -json=<jsonfile> parameter to the http_proxy_standalone.sh script. For example:
... -json="myfilters.json"
The config file can be uploaded to the Mamori server to manage the configuration in the server.
The JSON file configuration format is an array of API filters which define the rules for intercepting incoming HTTP/S client requests. Each filter specifies the interception criteria and and one or more MASK transformations to apply to the API response data.
- each filter defines a series of matching conditions to be able to identify which client HTTP request to intercept
- each transformation specifies the response attributes to mask
elementSpecand the MASK function to applyfunction
For example:
[
{
"name": "REST API",
"system": "testsystem",
"path": "/my-rest-api", <-- API endpoint to target
"method": null,
"queryParameters": null,
"headers": null,
"body": null,
"owner": "test",
"active": 1,
"transformations": [
{
"name": "default", <-- user/role to apply to
"priority": 1,
"elementSpec": "$..price", <-- JSON PATH for all price fields
"function": "MASK FULL", <-- Masking function to apply
}
]
},
{
"name": "XML API",
"system": "testsystem",
"path": "/my-xml-api", <-- API endpoint to target
"method": null,
"queryParameters": null,
"headers": null,
"body": null,
"owner": "test",
"active": 1,
"transformations": [
{
"name": "default", <-- user/role to apply to
"priority": 1,
"elementSpec": "//salary", <-- XML PATH for all salary fields
"function": "MASK FULL", <-- Masking function to apply
}
]
}
]
name- the filter/rule namesystem- the system to apply the rule topath- the HTTP request URL path to match on (regexp e.g .* is supported) e.g /infomethod- the HTTP request method to match on e.g GET, POST, PUTqueryParameters- the HTTP request query parameters e.g op=getUserDataheaders- the HTTP request headers to match on e.g X-OP=getUserDatabody- the HTTP request body to match on e.g (regexp e.g .* is supported) e.g .*SOMEKEY
*Transformations - specify fields to mask **
To specify which response fields/attributes to mask set the filter attribute elementSpec.
The proxy supports 2 elementSpec types:
-
For JSON data use json-path, which can be tested at Online json-path tester
-
For SOAP/XML data use XPath, which can be tested at Online XPath tester
For example:
To target all title fields in a JSON response use the JSON path:
$..title
To target all title fields in an XML response us the XML path:
//title
Note, if the XML payload uses namespaces (as is common in SOAP responses) you must specify the namespace in your xpath e.g //ns:title or use
local-name() if you don't know the specific namespace e.g //*\[local-name()='title'\].
Transformations - applying masking functions
Each transformation specifies the set of XML/JSON fields to target (elementSpec), the role/user that the transform applies too (name),and the mask/hash function to apply (function).
Masking function reference
| Function | Description |
|---|---|
| MASK ALL | Masks all characters with X or supplied mask character |
| MASK FIRST | Masks first N characters with X or supplied mask character |
| MASK LAST | Masks last N characters with X or supplied mask character |
| MASK SUBSTRING | Masks a substring (start,end) characters with X or supplied mask character |
| MASK CC | Masks the digits in a CC number |
| MASK SSN | Masks all digits in a SSN |
| MASK PHONE | Masks the last 4 digits of a phone number |
| MASK DATETIME | Generates a random datetime or adds a days. If the input is String the datetime format must be supplied as a function arg |
| MASK DATE | Generates a random date or adds a days. If the input is a String, the date format must be supplied as a function arg |
| MASK DECIMAL | Generates a random double to the specified number of digits and precision (decimals) |
| MASK INT | Generates a random long of the same length as the input |
| MASK EMAIL | Masks all characters with * or supplied mask character |
| MASK EMAIL KEEP SUFFIX | Masks domain characters with * or supplied mask character |
| MASK EMAIL KEEP DOMAIN | Masks suffix characters with * or supplied mask character |
| MASK OUT | Masks the first % with X or supplied mask character. Percentage defaults to 0.6 if not specified |
| MASK RANDOM | Masks letters and digits with randomly generated letters and digits |
| MASK HASH | Masks letters and digits with supplied hashing function e.g "MD5" |
| MASK HASH NUMERIC | Masks letters and digits with supplied hashing function e.g "SHA-1" to supplied length |
| MASK ROW | QLIK only. Masks all rows where the column value matches the supplied regexp in the function args. |
| REVEAL | Reveal a masked attribute |
Dealing with SSL
Overview
By default the application/API proxies use a self signed certificate. Some browsers such as Chrome (and also curl) will raise an SSL error if you attempt to use HTTPS to access your API via the proxy.
Bypass the certificate check
If using CURL you can bypass the certificate check by using the curl flag --insecure.
For some browsers, it is possible to configure the browser to ignore the cert check.
Otherwise, you can either configure the proxy to use a valid certificate and private key for the domain you are proxying or deploy the proxy behind HAPROXY or NGINX or APACHE which handles the SSL terminator - this is the recommended option.
To use a certificate and key with a proxy
To add a cert/key, configure the location of the certificate and key files in config/proxy-<system>.properties:
mockserver.dynamicallyCreateCertificateAuthorityCertificate=false
mockserver.privateKeyPath=... <-- your private key file
mockserver.x509CertificatePath=...<-- your certificate file
To generate a certificate for your domain you can use sites such as letsencrypt.org.
Example SSL/proxy forward NGINX config
An example NGINX for handling SSL and forwarding to a Qlik proxy running on a local port.
upstream qlik {
server 127.0.0.1:8080; <-- Qlik proxy
}
server {
server_name qlik.foo.com;
listen 80;
listen [::]:80;
root /var/www/html;
index some-file-that-does-not-exist;
error_page 403 @gotohttps;
error_page 404 @gotohttps;
location / {
try_files $uri $uri/ =404;
}
location @gotohttps {
rewrite ^ https://$host$request_uri permanent;
}
}
map $http_upgrade $connection_upgrade {
default upgrade;
'' close;
}
server {
server_name qlik.foo.com;
# SSL configuration
#
listen 443 ssl http2;
listen [::]:443 ssl http2;
index index.html;
root /var/www/html;
ssl_certificate /etc/nginx/ssl/nginx.crt;
ssl_certificate_key /etc/nginx/ssl/nginx.key;
location / {
proxy_pass http://qlik/;
proxy_redirect off;
proxy_http_version 1.1;
proxy_set_header X-Forwarded-For $remote_addr;
proxy_set_header Connection $connection_upgrade;
proxy_set_header Upgrade $http_upgrade;
proxy_read_timeout 7d;
proxy_send_timeout 7d;
}
}
Extracting the user from an HTTP/S request
Out of the box the application/API proxies provide two mechanisms to identify the requesting user:
-
Simple - extracts user details from a request header, query parameter or form field using a simple regular-expression based mechanism. This mechanism works with schemes such as Basic Authorisation.
-
Token - Maps a token to a user. This assumes signin occurs via the proxy and can only be used in a non clustered environment.
Method one: Simple
-
Open the
config/proxy-<system>.propertiesconfiguration file in a terminal window. -
Set the user extraction mechanism to
simpleauth. Add the following configuration to extract the user from a requestAuthorizationHTTP header:
authentication=simpleauth
simpleauth.header=Authorization <-- or simpleauth.formfield=user or simpleauth.queryparam=user or simpleauth.body.regexp=.. or simpleauth.body=xpath or json path
simpleauth.header.regexp=.*
Will handle basic Authorization:
Authorization: Basic QWxhZGRpbjpPcGVuU2VzYW1l <-- user is extracted as Aladdin
Alternatively, if using a different header, specify that and use a Regular Expression to extract the username from the header value:
simpleauth.header=MySpecialAuthHeader <-- name of the header to use
simpleauth.header.regexp=.* <-- Optional Regular expression to extract the username from the header contents (can be null)
Method two: Token
This mechanism extracts the user name from a signin/login and tracks the token to allow the user to be identified on subsequent requests.
-
Open the
config/proxy-<system>.propertiesconfiguration file in a terminal window. -
Set the extraction mechanism to
tokenauth. Add the following configuration to extract the login token and user from an auth server
authentication=tokenauth
# Authorisation server
auth.remotehost=....
auth.remoteport=443
# On a user sign in
tokenauth.signin.path=(/users/sign_in|/users/session_data)
tokenauth.signin.method=
# User name and token extraction. Specify how to extract the user and token on sign in
tokenauth.user.body=$..email <-- can also be in a header, query parameter or form field or body
tokenauth.token.body=$..token <-- can also be in a header, query parameter or form field or body
# On a user signout
# Stops token from being tracked
tokenauth.signout.path=/users/sign_outec
tokenauth.signout.method=DELETE
# On all other requests extract token from token header
simpleauth.header=token
Once the user has been extracted, the proxy can determine the user's roles and determine which masking rules to apply.
Monitoring and Logging
By default the proxies publish various metrics about the JVM and endpoints to the proxy log and the Mamori server monitoring sub-system.
The metrics can be viewed inside the the Mamori server Influx/Grafana dashboards.
By default two monitoring channels are enabled:
- InfluxDb
- Proxy Log
More information on Influx configuration properties can be found at influx configuration
Upgrading Grafana
To upgrade Grafana run the command below in your Mamori server.
sudo docker exec -it mamori /opt/mamori/grafana/update-grafana.sh
To Activate
- Open the monitoring properties configuration file at
/opt/mamori/server/http-proxy-<version>/config/monitoring.properties. - Set the following properties:
influx.enabled=true
logging.enabled=true
To Deactivate
-
Open the monitoring properties file at
/opt/mamori/server/http-proxy-<version>/http-proxy-<version>/config/monitoring.properties. -
Set the following properties:
influx.enabled=false
logging.enabled=false
Proxy log files
- Application Proxy log --
/opt/mamori/server/http-proxy-<version>/log/proxy-<system>-<instance>.log - Service issues log --
/var/log/syslog
Proxy healthcheck endpoint
The proxy heartbeat/healthcheck is on http/s:<proxy host>:<port>/healthcheck. If the proxy is up, it will return a status 200.
=======
Basic Server Hardening
The steps below are only a basic hardening guide. Please check the current hardening guide for your OS.
Secure Shared Memory
#Open the file for editing by issuing the command:
sudo vi /etc/fstab
#Add the following line to the bottom of that file:
tmpfs /run/shm tmpfs defaults,noexec,nosuid 0 0
Secure logins
Set server to only accept key based logins. Enable SSH Logins to only allow specified IP address sources
sudo vi /etc/ssh/sshd_config
#only allow ssh for your desired IP addresses
AllowUsers *@192.168.1.*
#disable password logins
ChallengeResponseAuthentication no
PasswordAuthentication no
UsePAM no
PermitRootLogin prohibit-password
Reboot the server for changes to take effect
Install Fail2Ban
If your server is publicly accessible, then install fail2Ban
Wireguard
Verify Packets
Check if Wireguard packets are being forwarded to Mamori server
tcpdump -i any -n -x udp port 51871
MSQL SYNTAX
Mamori SQL (MSQL) allows you run SQL like syntax to configure your mamori server. MSQL can be run in the mamori console editor or via the msql utility that deploys with the server.
TEMPLATE
Below is an excel template that will generate MSQL for creating common resources
Date Functions
select dateadd(second, -36000, current_timestamp), current_utc_timestamp, current_timestamp from sys.dual
Background tasks & Pools
call BACKGROUND_TASKS();
call CONNECTION_POOLS();
LOGGING
#To generated detailed detailed statement pool metrics
#define LOG_STATEMENT_POOL_METRICS in /opt/mamori/var/mamori_env.local
MISC
#Get the attribute and values for an RDP definition
call GET_REMOTE_DESKTOP_CONNECTION_DETAILS('RDP NAME');
#Update the RDP properties that are passed in
call UPDATE_REMOTE_DESKTOP_ATTRIBUTES('RDP NAME', '{"enable_font_smoothing": true,"enable_wallpaper":true,"enable_theming":true}');
#To export a session
call EXPORT_SESSION_DETAILS('{AZBsPs6wdhnU6ymHMmulEA}')
#To send a notification to a mobile device
call create_user_notification('pushtestuser', 'pushmessage', 'this is a test');
#To Install certificates
Usage: msql install-cert [OPTIONS] --certificate <CERTIFICATE>
Options:
--certificate <CERTIFICATE> a file containing the PEM encoded certificate
--key <KEY> a file containing the PEM encoded private key
-h, --help Print help
#Benchmark Data Read Performances
#/opt/mamori/mamori/bin/msql
./msql --host MAMORISERVER --username user benchmark rms.db.schema.table
Mamori login Password Policies
-- See current policies
select * from "SYS"."SYSPOLICIES";
-- Example standard password policy
-- Changes to the policy will affect new passwords not existing ones.
-- It will not force users to reset current passwords.
alter policy password set options (password_length_minimum '12');
alter policy password set options (password_numeral_minimum '1');
alter policy password set options (password_punctuation_minimum '1');
alter policy password set options (password_upper_case_minimum '1');
alter policy password set options (password_expiration_days '60');
alter policy password set options (password_history_lockout '0');
alter policy password set options (inactivity_limit_days '0');
alter policy password set options (password_length_maximum '0');
alter policy password set options (password_lower_case_minimum '0');
alter policy password set options (password_character_type_minimum '0');
password_character_type_minimum,password_length_maximum,password_lower_case_minimum
--after this many failed logins, the account will be locked. Default: 10
alter policy password set options (failed_attempts_limit '10');
--how long an automatic lock will last for, in seconds. Default: 15
CALL SET_SERVER_PROPERTY('mamori.security.auto_lockout.minutes', '15');
(DISABLE | ENABLE) USER <username>
ALTER USER <username> LOCK [UNTIL timestamp]
ALTER USER <username> UNLOCK
Server Properties
-- Updating any property
call set_server_property('YOUR PROPERTY NAME', 'value');
-- Enable proxy detailed trace for just a specific user
call set_proxy_user_debug('USERNAME', true);
-- set server property with the name of the "rule" event handler
call set_server_property('on_failed_login', 'connection_failed');
--Enable One Time E-Mail 2FA - Defaults to true
call set_server_property('email_mfa_enabled', 'false');
--set server property with the name of the "policy" event handler
call set_server_property('on_request_handler', 'custom_on_request');
--how long a directory user must be known to be disabled before the user will be deleted by a sync. Default: 60
CALL SET_SERVER_PROPERTY('mamori.ldap.delete_delay.minutes', '60');
--How many devices can register the same MFA QRCode
call set_server_property('websocket_registration_flow', 'legacy');
Alert Settings
--This is the number of minutes to throttle any keyed alerts
call set_server_property('ALERT_THROTTLE_TIME', '5');
Email MFA support
-- disable Email MFA on the login screen
call set_server_property('email_mfa_enabled', 'false');
-- enable Email MFA on the login screen
call set_server_property('email_mfa_enabled', 'true');
DB Proxy TLS Protocol & Ciphers
Reboot server after changing this property.
-- Check existing mamori server settings
call TLS_SETTINGS()
-- Get Default Set Cipers
call set_server_property('enabled_tls_ciphers', 'default');
-- Specify Specfic Ciphers
call set_server_property('enabled_tls_ciphers', 'TLS_AES_256_GCM_SHA384,TLS_AES_128_GCM_SHA256,TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256,TLS_RSA_WITH_AES_256_GCM_SHA384,TLS_RSA_WITH_AES_128_GCM_SHA256');
--Specify Specfic Protocols
call set_server_property('enabled_tls_protocols', 'TLSv1.1,TLSv1.2,TLSv1.3');
Backup And Restore
All-In-One Install
To backup and restore on a new mamori server do the following:
- Run the backup script below on the source mamori server
- Tranfer mamori-backups to new target server with only docker. Mamori not installed
- Run the mamori-backups/restore.sh on target server
- Run the mamori install on target server
#!/bin/bash
HERE=`pwd`
mkdir -p mamori-backups
docker stop mamori
docker container inspect -f '{{ range .Mounts }}{{.Type}} {{ .Name }} {{ .Destination }}{{println}}{{ end }}' mamori | grep "^volume mamori" | awk '{print "cd " $3 " && tar zcvf /backups/" $2 ".tgz ." }' | docker run -i --rm --volumes-from mamori --volume $HERE/mamori-backups:/backups mamori-alpine-boringtun sh
docker image save mamori-alpine-boringtun | gzip > mamori-backups/mamori-alpine-boringtun.tgz
echo "#!/bin/sh" > mamori-backups/restore.sh
echo "docker load < mamori-alpine-boringtun.tgz" >> mamori-backups/restore.sh
docker container inspect -f '{{ range .Mounts }}{{.Type}} {{ .Name }} {{ .Destination }}{{println}}{{ end }}' mamori | grep "^volume mamori" | awk '{print "docker run --rm -it --volume " $2 ":" $3 " --volume $PWD:/backups mamori-alpine-boringtun sh -c \"cd " $3 " && tar zxvf /backups/" $2 ".tgz\""}' >> mamori-backups/restore.sh
create user mamori with password 'password';
grant all privileges on database mamorisys to mamori;
grant all privileges on database xcs to mamori;
grant all privileges on database audit to mamori;
\c mamorisys
grant all on schema rms to mamori;
grant all on all tables in schema rms to mamori;
grant all on all sequences in schema rms to mamori;
grant all on schema fqo to mamori;
grant all on all tables in schema fqo to mamori;
grant all on all sequences in schema fqo to mamori;
grant all on schema rms to mamori;
grant all on all tables in schema rms to mamori;
grant all on all sequences in schema rms to mamori;
grant all on schema mamorisys to mamori;
grant all on all tables in schema mamorisys to mamori;
grant all on all sequences in schema mamorisys to mamori;
grant all on schema public to mamori;
grant all on all tables in schema public to mamori;
grant all on all sequences in schema public to mamori;
grant all on schema security to mamori;
grant all on all tables in schema security to mamori;
grant all on all sequences in schema security to mamori;
\c xcs
grant all on schema public to mamori;
grant all on all tables in schema public to mamori;
grant all on all sequences in schema public to mamori;
\c audit
grant all on schema audit to mamori;
grant all on all tables in schema audit to mamori;
grant all on all sequences in schema audit to mamori;
grant all on schema public to mamori;
grant all on all tables in schema public to mamori;
grant all on all sequences in schema public to mamori;
/opt/mamori/mamori/bin/set_pg_password.sh --username lkj --password kjh --host asdsad --port
create user mamori with password 'password';
grant all privileges on database mamorisys to mamori;
grant all privileges on database xcs to mamori;
grant all privileges on database audit to mamori;
\c mamorisys
grant all on schema rms to mamori;
grant all on all tables in schema rms to mamori;
grant all on all sequences in schema rms to mamori;
grant all on schema fqo to mamori;
grant all on all tables in schema fqo to mamori;
grant all on all sequences in schema fqo to mamori;
grant all on schema rms to mamori;
grant all on all tables in schema rms to mamori;
grant all on all sequences in schema rms to mamori;
grant all on schema mamorisys to mamori;
grant all on all tables in schema mamorisys to mamori;
grant all on all sequences in schema mamorisys to mamori;
grant all on schema public to mamori;
grant all on all tables in schema public to mamori;
grant all on all sequences in schema public to mamori;
grant all on schema security to mamori;
grant all on all tables in schema security to mamori;
grant all on all sequences in schema security to mamori;
\c xcs
grant all on schema public to mamori;
grant all on all tables in schema public to mamori;
grant all on all sequences in schema public to mamori;
\c audit
grant all on schema audit to mamori;
grant all on all tables in schema audit to mamori;
grant all on all sequences in schema audit to mamori;
grant all on schema public to mamori;
grant all on all tables in schema public to mamori;
grant all on all sequences in schema public to mamori;
/opt/mamori/mamori/bin/set_pg_password.sh --username lkj --password kjh --host asdsad --port
Update PG MAX Connections
All-In-One Install
1 - Enter docker
2 - Update /opt/mamori/var/mamori_env.local to change the value of POSTGRES_MAX_CONNECTIONS
3 - Exit the docker
4 - restart the docker container
Upgrading Docker
Docker does not have a specific upgrade command. To upgrade Docker, you need to remove the old version and install the new one. This process will not impact your data as Docker volumes and containers are preserved.
To upgrade Docker, run the following script:
#!/bin/bash
# Remove old Docker versions
sudo apt remove docker docker-engine docker.io containerd runc
# Update package index
sudo apt update
# Install prerequisites
sudo apt install apt-transport-https ca-certificates curl gnupg lsb-release
# Add Docker's official GPG key
curl -fsSL https://download.docker.com/linux/ubuntu/gpg | sudo gpg --dearmor -o /usr/share/keyrings/docker-archive-keyring.gpg
# Add Docker repository
echo "deb [arch=$(dpkg --print-architecture) signed-by=/usr/share/keyrings/docker-archive-keyring.gpg] https://download.docker.com/linux/ubuntu $(lsb_release -cs) stable" | sudo tee /etc/apt/sources.list.d/docker.list > /dev/null
# Update package index again
sudo apt update
# Install Docker Engine
sudo apt install docker-ce docker-ce-cli containerd.io docker-buildx-plugin docker-compose-plugin
# Verify installation
docker --version