Overview
Mamori has a robust policy engine that allows you to meet all you audit and security requirements. Session policies govern connections coming in via Mamori and access policies govern the resources that a login either will have or can request access to. There are five types of session policies and three types of access policies.
Session Policies
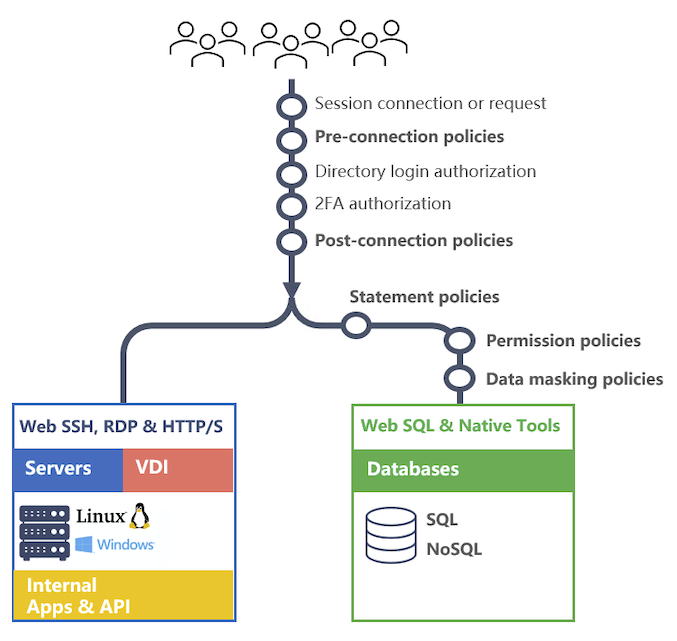
Session policies allow you define rules based on properties of the session to block, audit and alert on SSH, SFTP, RDP, HTTP/S, TCP and database activity. Additionaly for database sessions you can provide permission, data masking and row/column security.
- Pre-connection policies - trigger before any authentication processing.
- Post-connection policies - trigger after a valid authentication process.
- DB Statement policies - trigger for database commands prior to accessing database catalogs.
- DB Permission policies - trigger for database commands and access the database catalogs.
- Data Masking policies - trigger on incoming database commands and rewrite the statement.
No, Mamori automatically records all database connections and statements in a seperate log that is easy to query and extract data from.
Create custom policies only if you want block, alert on or audit specific activity like after hours access to a production database.
Access Policies
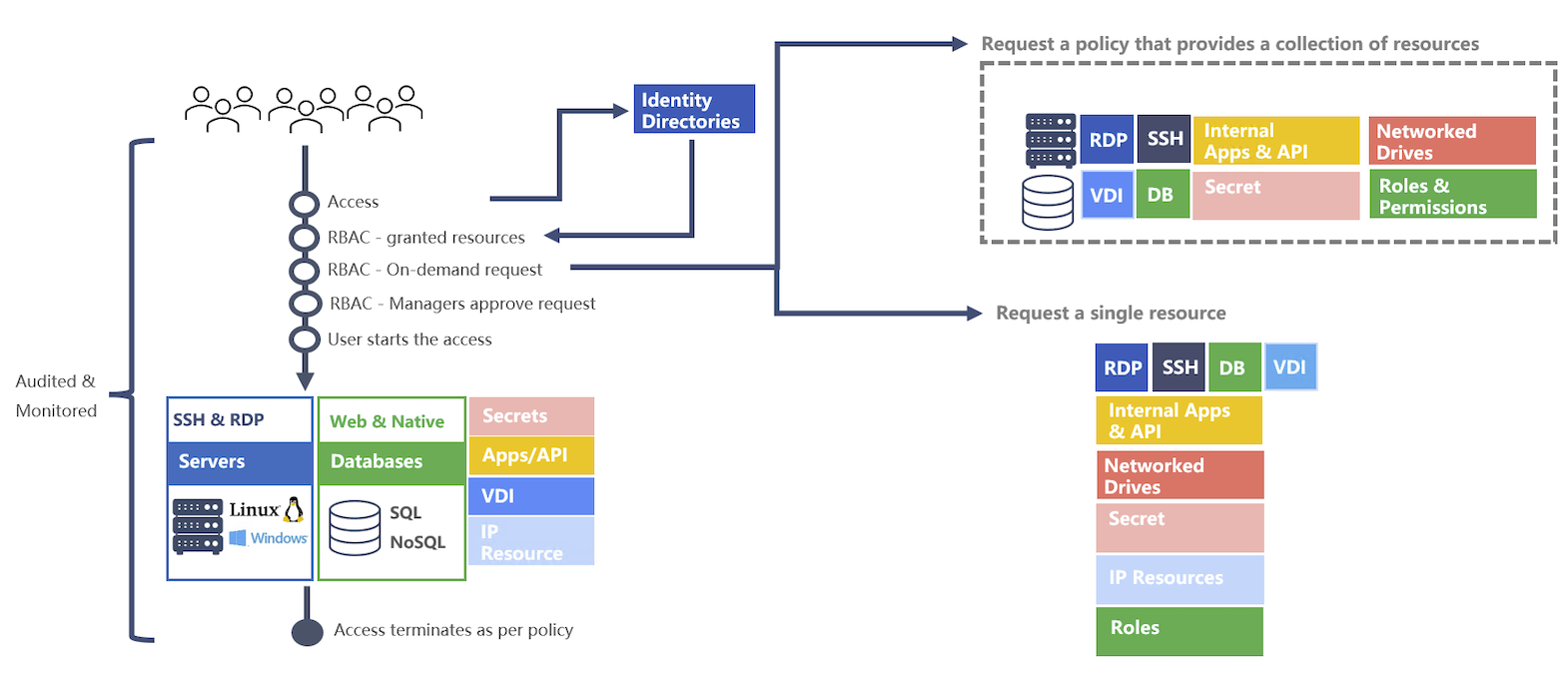
Access policies provide users with either permanent permissions on resources or the ability to request permissions on a resource. Administrators manage both who is able to request and endorse which policies and resources.
- Grants - permanent or time based permissions granted to a user or Mamori role. Allows segmentation of the existing permissions a database credential has.
- On-demand policies - Request and endorse a policy that grants permissions on a custom set of resources.
- On-demand resource policies - Request and endorse access to a particular resource.
Users and endorsers can use either the Mamori mobile app or the Mamori web portal to request or endorse resources.