Proxy Access
Overview
Use this access method if you want to
The Mamori server has built-in proxies for HTTP/S, SSH and database connections. It is recommended that you first use the web console to configure and verify resource access, and then try the proxy access.
Configuration Steps
Prerequisites
Step 1 - Confirm connections from client
If this is required for a critial application, then have one HA Mamori server for the application traffic and another for the ad hoc traffic
Database Access Controls
The Mamori proxies handle native connections for the 5 main database wire protocols (Oracle, MySQL, Postgres, MS SQL Server & MongoDB). Any database that uses the same wire protocol are also supported. For example, greenplum, redshift and cockroach DB are supported because they use the postgres wire protocol.
Databases, like teradata and impala, are supported via the Mamori client jdbc and odbc driver.
Configuration Steps
Step 1 - Login to the web portal & verify you have access to the target database via WebSQL
Step 2 - Verify connection to the target database from desired client tools
Client tool connection settings
To connect via the Mamori server from your database tools update the connection strings as per the table below
Connection Without Mamori Via Mamori Host the database ip the Mamori server ip Port the database listener the Mamori proxy port. See Ports Database the database name the alias in Mamori for the database Authentication database credentials Mamori SSO + 2FA
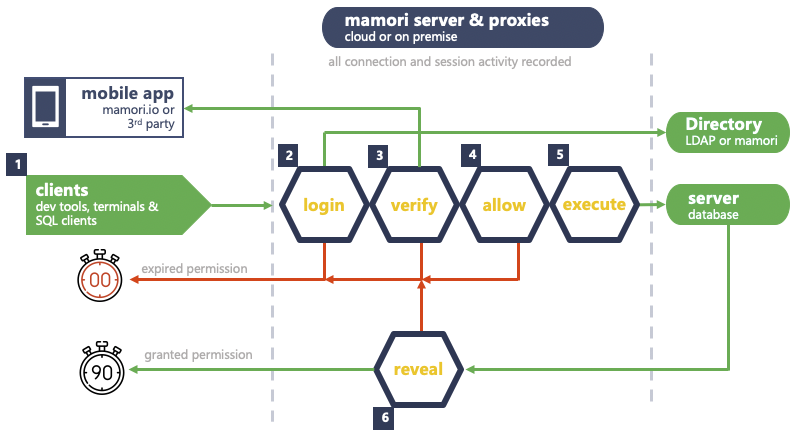
Proxy Workflow
SSH Logins
SSH connections via the proxy only supports connecting to SSH logins configured to use public key authentication. Each user must upload their private key that will be verified on an SSH login request. Shared public keys across user accounts is not permitted.
Connecting
To ssh via Mamori you need ensure you have added a public ssh key to your Mamori account. Follow the instructions below to add your public ssh key.
Login to the Mamori portal
Click on your login name to see your profile menu
Click SSH & SERVER ACCESS
Click PUBLIC SSH KEY
Set the properties
Field Description Name Your reference for the key Public Key Paste in your public key Click ADD KEY
Make an ssh connection from a terminal or tool
ssh -p sshproxyport thesshlogin@mamoriserver -- example ssh -p 1122 prodserver@mymamoriserver
click here for instructions on how to view your current SSH proxy port.